Everyone understands that the longer the Cisco certification exam is delayed, the less patience will be, and passing as soon as possible is the best choice. The Cisco 200-201 dumps have been updated to help you prepare for the Cisco CyberOps Associate CBROPS exam. Pass4itSure’s updated 200-201 dumps are the best exam preparation material with 245+ real exam questions and answers (PDF+VCE) that will surely help you prepare for the exam and earn your CyberOps Associate certification.

Get updated Cisco 200-201 dumps: https://www.pass4itsure.com/200-201.html Updated: Apr 27, 2022, prepare for exams with ease.
You can practice free dumps first:
QUESTION 1
How does an attacker observe network traffic exchanged between two users?
A. port scanning
B. man-in-the-middle
C. command injection
D. denial of service
QUESTION 2
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
A. file extension associations
B. hardware, software, and security settings for the system
C. currently logged in users, including folders and control panel settings
D. all users on the system, including visual settings
QUESTION 3
What is threat hunting?
A. Managing a vulnerability assessment report to mitigate potential threats.
B. Focusing on proactively detecting possible signs of intrusion and compromise.
C. Pursuing competitors and adversaries to infiltrate their system to acquire intelligence data.
D. Attempting to deliberately disrupt servers by altering their availability
QUESTION 4
Refer to the exhibit.
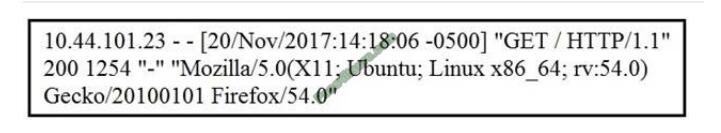
What does the message indicate?
A. an access attempt was made from the Mosaic web browser
B. a successful access attempt was made to retrieve the password file
C. a successful access attempt was made to retrieve the root of the website
D. a denied access attempt was made to retrieve the password file
QUESTION 5
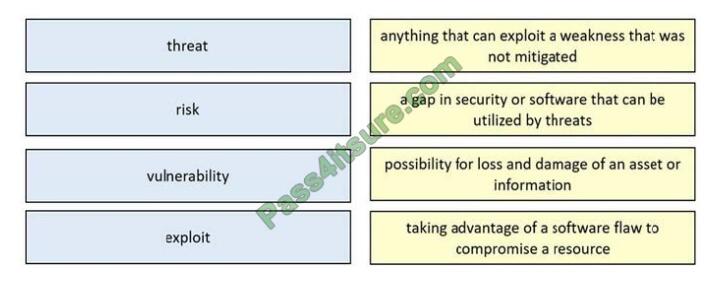
DRAG-DROP
Drag and drop the security concept from the left onto the example of that concept on the right.
Select and Place:
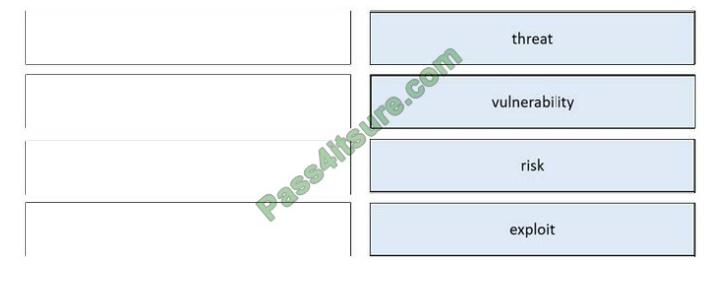
Correct Answer:
QUESTION 6
Which two elements are assets in the role of attribution in an investigation? (Choose two.)
A. context
B. session
C. laptop
D. firewall logs
E. threat actor
The following are some factors that are used during attribution in an investigation: Assets, Threat actor, Indicators of Compromise (IoCs), Indicators of Attack (IoAs), and Chain of custody Asset: This factor identifies which assets were compromised by a threat actor or hacker. An example of an asset can be an organization\\’s domain controller (DC) that runs Active Directory Domain Services (AD DS).
AD is a service that allows an administrator to manage user accounts, user groups, and policies across a Microsoft Windows environment. Keep in mind that an asset is anything that has value to an organization; it can be something physical, digital, or even people. Cisco Certified CyberOps Associate 200-201 Certification Guide
QUESTION 7
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
A. Untampered images are used in the security investigation process
B. Tampered images are used in the security investigation process
C. The image has tampered if the stored hash and the computed hash match
D. Tampered images are used in the incident recovery process
E. The image is untampered if the stored hash and the computed hash match
Cert Guide by Omar Santos, Chapter 9 – Introduction to Digital Forensics. “When you collect evidence, you must protect its integrity. This involves making sure that nothing is added to the evidence and that nothing is deleted or destroyed (this is known as evidence preservation).”
QUESTION 8
Refer to the exhibit.
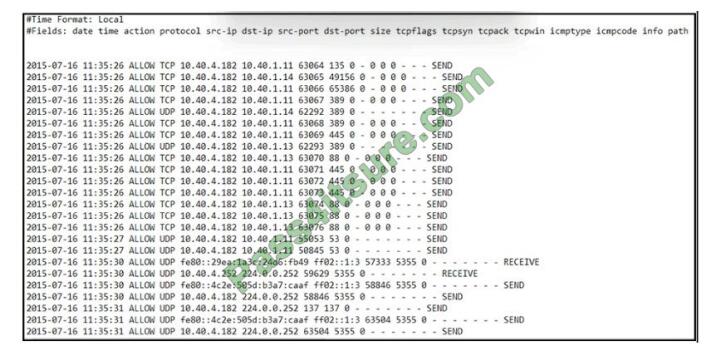
An engineer received an event log file to review. Which technology generated the log?
A. NetFlow
B. proxy
C. firewall
D. IDS/IPS
QUESTION 9
Refer to the exhibit.
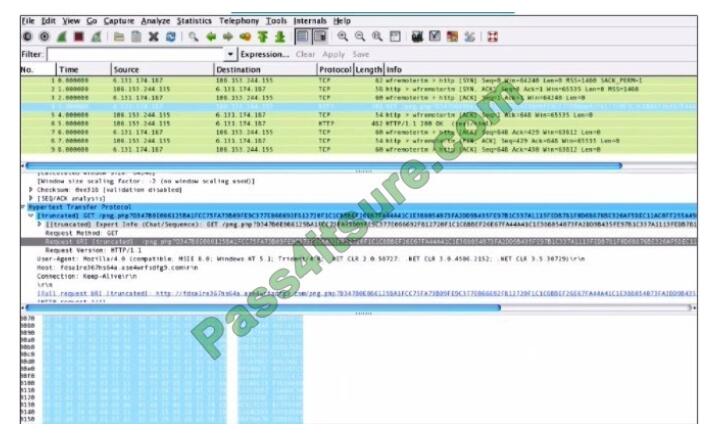
What is shown in this PCAP file?
A. Timestamps are indicated with error.
B. The protocol is TCP.
C. The User-Agent is Mozilla/5.0.
D. The HTTP GET is encoded.
QUESTION 10
What is the difference between a threat and a risk?
A. Threat represents a potential danger that could take advantage of a weakness in a system
B. Risk represents the known and identified loss or danger in the system
C. Risk represents the nonintentional interaction with uncertainty in the system
D. Threat represents a state of being exposed to an attack or a compromise, either physically or logically.
A threat is any potential danger to an asset. If a vulnerability exists but has not yet been exploited–or, more importantly, it is not yet publicly known–the threat is latent and not yet realized.
QUESTION 11
Which step in the incident response process researches an attacking host through logs in a SIEM?
A. detection and analysis
B. preparation
C. eradication
D. containment
Preparation –> Detection and Analysis –> Containment, Eradication and Recovery –> Post-Incident Activity Detection and Analysis –> Profile networks and systems, Understand normal behaviors, Create a log retention policy, Perform event correlation. Maintain and use a knowledge base of information. Use Internet search engines for research.
Run packet sniffers to collect additional data. Filter the data. Seek assistance from others. Keep all host clocks synchronized. Know the different types of attacks and attack vectors. Develop processes and procedures to recognize the signs of an incident. Understand the sources of precursors and indicators. Create appropriate incident documentation capabilities and processes. Create processes to effectively prioritize security incidents. Create processes to effectively communicate incident information (internal and external communications).
Ref: Cisco CyberOps Associate CBROPS 200-201 Official Cert Guide
QUESTION 12
What is the difference between data obtained from Tap and SPAN ports?
A. Tap mirrors existing traffic from specified ports, while SPAN presents more structured data for deeper analysis.
B. SPAN passively splits traffic between a network device and the network without altering it, while Tap alters response times.
C. SPAN improves the detection of media errors, while Tap provides direct access to traffic with lowered data visibility.
D. Tap sends traffic from physical layers to the monitoring device, while SPAN provides a copy of network traffic from switch to destination
Reference: https://www.gigamon.com/resources/resource-library/white-paper/to-tap-or-to- span.html
QUESTION 13
What is the difference between inline traffic interrogation and traffic mirroring?
A. Inline interrogation is less complex as traffic mirroring applies additional tags to data.
B. Traffic mirroring copies the traffic rather than forwarding it directly to the analysis tools
C. Inline replicates the traffic to preserve integrity rather than modifying packets before sending them to other analysis tools.
D. Traffic mirroring results in faster traffic analysis and inline is considerably slower due to latency.
Correct answer:
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| B | B | A | C | see picture | CD | AE | C | D | A | A | D | A |
13 Updated 200-201 (CBROPS) Exam Question Answers
Free 200-201 exam questions PDF download: https://drive.google.com/file/d/1qCbxbEgp2Vb4WArxsYhLJk3iaR3Ciuse/view?usp=sharing
Get ready, Pass4itSure 200-201 Dumps: https://www.pass4itsure.com/200-201.html is your best bet for the easy success in the Three Hunting and Defending using Cisco Technologies for CyberOps (CBROPS) exams.