
To pass the CompTIA A+ Certification Exam: Core 2 exam more efficiently, you should get the latest CompTIA A+ 220-1102 dumps practice questions 2024, which will help you pass the exam efficiently.
Here you can download 220-1102 dumps 2024 https://www.pass4itsure.com/220-1102.html (you can choose PDF or VCE mode) to get 220-1102 practice questions 2024 for practical exercises to pass the exam.
Of course, we also have prepared free 220-1102 dumps practice questions for everyone (new in 2024).
220-1102 dumps 2024 keeping up with the times
Take an example, and you’ll get the idea. Will the 220-1102 dumps in January 2024 apply to your April exam? No. As the time passes, the exam will change.
CompTIA A+ exam 220-1102 is changing: Examining emerging technologies, security protocols, and best practices has been added to reflect the latest trends and requirements in the industry. The exam may introduce more real-world application or case analysis questions to test candidates’ ability to solve problems in real-world work situations.
So as a good 220-1102 dumps we also updated the following: new 220-1102 exam practice questions
They are based on the 220-1102 dumps updated in January and the 220-1102 dumps updated in April. Welcome to compare and learn.
CompTIA A+ 220-1102 dumps and practice questions shared online (January 2024)
| Pass4itSure | 1-15(516) | CompTIA A+ |
Question 1:
A user needs assistance changing the desktop wallpaper on a Windows 10 computer. Which methods will enable the user to change the wallpaper using a Windows 10 Settings tool?
A. Open Settings, select Accounts, select, Your info, click Browse, and then locate and open the image the user wants to use as the wallpaper
B. Open Settings, select Personalization, click Browse, and then locate and open the image the user wants to use as the wallpaper
C. Open Settings, select System, select Display, click Browse, and then locate and open the image the user wants to use as the wallpaper
D. Open Settings, select Apps, select Apps and Features, click Browse, and then locate and open the image the user wants to use as the wallpaper.
Correct Answer: B
To change the desktop wallpaper on a Windows 10 computer using a Windows 10 Settings tool, the user should open Settings, select Personalization, click Browse, and then locate and open the image the user wants to use as the wallpaper https://www.lifewire.com/change-desktop-background-windows-11-5190733
Question 2:
A company discovered that numerous computers from multiple geographic locations are sending a very high number of connection requests which is causing the company\’s web server to become unavailable to the general public. Which of the following attacks is occurring?
A. Zero-day
B. SOL injection
C. Cross-site scripting
D. Distributed denial of service
Correct Answer: D
The company is experiencing a distributed denial of service (DDoS) attack. A DDoS attack is a type of cyber attack in which multiple compromised systems are used to target a single system, causing a denial of service for users of the targeted system.
Question 3:
A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message and no changes have been made within the company. Which of the following has infected the computer?
A. Cryptominer
B. Phishing
C. Ransomware
D. Keylogger
Correct Answer: C
Ransomware is malicious software that encrypts files on a computer, making them inaccessible until a ransom is paid. In this case, the user was able to access the files before without issue, and no changes have been made within the company, so the computer was likely infected with ransomware.
Question 4:
A technician is in the process of installing a new hard drive on a server but is called away to another task. The drive has been unpackaged and left on a desk. Which of the following should the technician perform before leaving?
A. Ask coworkers to make sure no one touches the hard drive.
B. Leave the hard drive on the table; it will be okay while the other task is completed.
C. Place the hard drive in an antistatic bag and secure the area containing the hard drive.
D. Connect an electrostatic discharge strap to the drive.
Correct Answer: C
The technician should place the hard drive in an antistatic bag and secure the area containing the hard drive before leaving. This will protect the hard drive from electrostatic discharge (ESD), dust, moisture, and physical damage. Asking coworkers to make sure no one touches the hard drive is not a reliable or secure way to prevent damage. Leaving the hard drive on the table exposes it to ESD and other environmental hazards. Connecting an electrostatic discharge strap to the drive is not enough to protect it from dust, moisture, and physical damage.
Question 5:
A bank would like to enhance building security to prevent vehicles from driving into the building while also maintaining easy access for customers. Which of the following BEST addresses this need?
A. Guards
B. Bollards
C. Motion sensors
D. Access control vestibule
Correct Answer: B
Bollards are the best solution to enhance building security to prevent vehicles from driving into the building while also maintaining easy access for customers4 References: 2. Bollards. Retrieved from https://en.wikipedia.org/wiki/ Bollard
Question 6:
A Windows user recently replaced a computer The user can access the public internet on the computer; however, an internal site at https7/companyintranet.com:8888 is no longer loading. Which of the following should a technician adjust to resolve the issue?
A. Default gateway settings
B. DHCP settings
C. IP address settings
D. Firewall settings
E. Antivirus settings
Correct Answer: D
The technician should adjust the firewall settings to resolve the issue of not being able to access an internal site at https://companyintranet.com:8888. The firewall settings control how the firewall filters and allows network traffic based on rules and policies.
The firewall settings may be blocking or preventing access to the internal site by mistake or by default, especially if the site uses a non-standard port number such as 8888. The technician should check and modify the firewall settings to allow access to the internal site or its port number.
Default gateway settings determine how a computer connects to other networks or the internet. Default gateway settings are not likely to cause the issue of not being able to access an internal site if the user can access the public internet. DHCP settings determine how a computer obtains its IP address and other network configuration parameters automatically from a DHCP server.
DHCP settings are not likely to cause the issue of not being able to access an internal site if the user can access other network resources. IP address settings determine how a computer identifies itself and communicates with other devices on a network. IP address settings are not likely to cause the issue of not being able to access an internal site if the user can access other network resources.
Antivirus settings control how the antivirus software scans and protects the computer from malware and threats. Antivirus settings are less likely to cause the issue of not being able to access an internal site than firewall settings unless the antivirus software has a firewall feature that may interfere with the network traffic. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 1.6
Question 7:
An employee calls the help desk regarding an issue with a laptop PC. After a Windows update, the user can no longer use certain locally attached devices, and a reboot has not fixed the issue. Which of the following should the technician perform to fix the issue?
A. Disable the Windows Update service.
B. Check for updates.
C. Restore hidden updates.
D. Rollback updates.
Correct Answer: D
The technician should perform a rollback of the Windows update that caused the issue with the locally attached devices. A rollback is a process of uninstalling an update and restoring the previous version of the system. This can help to fix any compatibility or performance issues caused by the update.
To roll back an update, the technician can use the Settings app, the Control Panel, or the System Restore feature. The technician should also check for any device driver updates that might be needed after rolling back the update. Disabling the Windows Update service is not a good practice, as it can prevent the system from receiving important security and feature updates.
Checking for updates might not fix the issue, as the update that caused the issue might still be installed. Restoring hidden updates is not relevant, as it only applies to updates that have been hidden by the user to prevent them from being installed.
References: https://www.windowscentral.com/how-uninstall-and-reinstall-updates-windows-10 https://support.microsoft.com/en-us/windows/show-or-hide-updates-in-windows-10-9c9f0a4f-9a6e-4c8e-8b44-afbc6b33f3cf‘
Question 8:
SIMULATION
The network administrator has changed the IP address of Computer A from 192. 168. 120 to 10. 10. 1020 and now Jane a user, is unable to connect to file shares on Computer A from Computers using the computer name.
Instructions:
Using the available tools, resolve the connectivity issues. When you have completed the simulation, please select the done button to submit your answer.
A. Please review the explanation for the detailed answer
Correct Answer: A
Please check the below images for detailed connectivity steps to do:
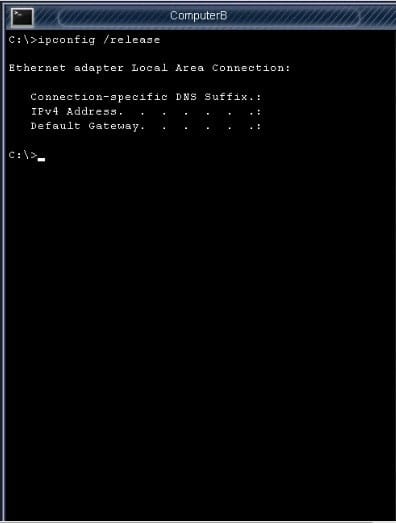
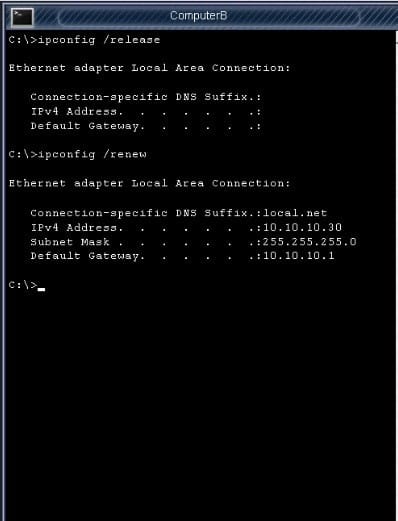
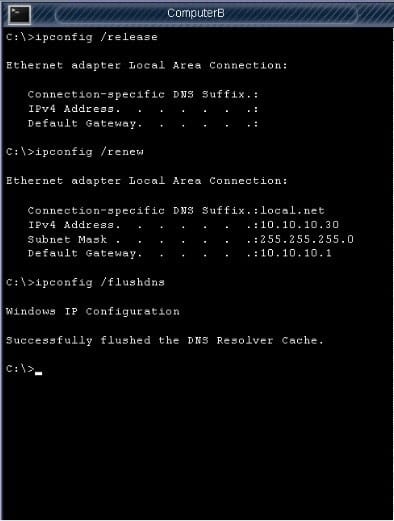
Question 9:
A developer\’s Type 2 hypervisor is performing inadequately when compiling new source code. Which of the following components should the developer upgrade to improve the hypervisor\’s performance?
A. Amount of system RAM
B. NIC performance
C. Storage IOPS
D. Dedicated GPU
Correct Answer: A
Question 10:
A technician wants to enable BitLocker on a Windows 10 laptop and is unable to find the BitLocker Drive Encryption menu item in the Control Panel. Which of the following explains why the technician is unable to find this menu item?
A. The hardware does not meet BitLocker\’s minimum system requirements.
B. BitLocker was renamed for Windows 10.
C. BitLocker is not included on Windows 10 Home.
D. BitLocker was disabled in the registry of the laptop
Correct Answer: C
BitLocker is only available on Windows 10 Pro, Enterprise, and Education editions1. Therefore, the technician is unable to find the BitLocker Drive Encryption menu item in the Control Panel because it is not included in the Windows 10 Home edition1.
Question 11:
A change advisory board authorized a setting change so a technician is permitted to implement the change. The technician successfully implemented the change. Which of the following should be done NEXT?
A. Document the date and time of change.
B. Document the purpose of the change.
C. Document the risk level.
D. Document findings of the sandbox test.
Correct Answer: A
After implementing a change authorized by the change advisory board (CAB), the technician should document the date and time of change as part of the post-implementation review. This helps to track the change history, verify the success of the change, and identify any issues or incidents caused by the change.
Documenting the purpose of the change, the risk level, and the findings of the sandbox test are all part of the pre-implementation activities that should be done before submitting the change request to the CAB.
References: https://www.manageengine.com/products/service-desk/itil-change-management/cab-change-advisory-board.html https://www.servicenow.com/content/dam/servicenow-assets/public/en-us/doc-type/success/quick-answer/change-advisory-board-setup.pdf
Question 12:
A macOS user is installing a new application. Which of the following system directories is the software MOST likely to install by default?
A. /etc/services
B. /Applications
C. /usr/bin
D. C:\Program Files
Correct Answer: B
The software is most likely to install by default in the /Applications directory, which is the standard location for macOS applications. This directory can be accessed from the Finder sidebar or by choosing Go > Applications from the menu bar.
The /Applications directory contains all the applications that are available to all users on the system. Some applications might also offer the option to install in the ~/Applications directory, which is a personal applications folder for a single user.
The /etc/services directory is a system configuration file that maps service names to port numbers and protocols. The /usr/bin directory is a system directory that contains executable binaries for various commands and utilities. The C: \Program Files directory is a Windows directory that does not exist on macOS.
Question 13:
A technician needs to document who had possession of evidence at every step of the process. Which of the following does this process describe?
A. Rights Management
B. Audit trail
C. Chain of custody
D. Data integrity
Correct Answer: C
The process of documenting who had possession of evidence at every step of the process is called chain of custody
Question 14:
A technician needs to recommend the best backup method that will mitigate ransomware attacks. Only a few files are regularly modified, however, storage space is a concern. Which of the following backup methods would BEST address these concerns?
A. Full
B. Differential
C. Off-site
D. Grandfather-father-son
Correct Answer: B
The differential backup method would best address these concerns. Differential backups only back up files that have changed since the last full backup, which means that only a few files would be backed up each time.
This would help to mitigate the risk of ransomware attacks, as only a few files would be affected if an attack occurred. Additionally, differential backups require less storage space than full backups.
Question 15:
Antivirus software indicates that a workstation is infected with ransomware that cannot be quarantined. Which of the following should be performed FIRST to prevent further damage to the host and other systems?
A. Power off the machine.
B. Run a full antivirus scan.
C. Remove the LAN card.
D. Install a different endpoint solution.
Correct Answer: A
Ransomware is a type of malware that encrypts the files on a system and demands a ransom for their decryption. Ransomware can also spread to other systems on the network or exfiltrate sensitive data to the attackers. Therefore, it is important to isolate the infected machine as soon as possible to contain the infection and prevent further damage.
Powering off the machine is a quick and effective way of disconnecting it from the network and stopping any malicious processes running on it. The other options are not directly related to preventing ransomware damage or may not be effective. Running a full antivirus scan may not be able to detect or remove the ransomware, especially if it is a new or unknown variant.
Removing the LAN card may disconnect the machine from the network, but it may not stop any malicious processes running on it or any data encryption or exfiltration that has already occurred. Installing a different endpoint solution may not be possible or helpful if the system is already infected and locked by ransomware.
New 220-1102 exam practice questions(April 2024)
| Pass4itSure | 1-8(592) | CompTIA A+ |
Q1:
A technician installs specialized software on a workstation. The technician then attempts to run the software. The workstation displays a message indicating the software is not authorized to run. Which of the following should the technician do to most likely resolve the issue?
A. Install the software in safe mode.
B. Attach the external hardware token.
C. Install OS updates.
D. Restart the workstation after installation
Correct Answer: B
Q2:
Which of the following defines the extent of a change?
A. Scope
B. Purpose
C. Analysis
D. Impact
Correct Answer: A
The term that defines the extent of a change in scope. Scope is a measure of the size, scale, and boundaries of a project or an activity. Scope defines what is included and excluded in the project or activity, such as goals, requirements, deliverables, tasks, and resources. Scope helps determine the feasibility, duration, and cost of the project or activity. Scope also helps manage the expectations and needs of the stakeholders involved in the project or activity. Purpose is the reason or objective for doing a project or an activity.
Purpose defines why the project or activity is important or necessary, such as solving a problem, meeting a need, or achieving a goal. Purpose helps provide direction, motivation, and justification for the project or activity. Analysis is the process of examining, evaluating, and interpreting data or information related to a project or an activity. Analysis helps identify, understand, and prioritize issues, risks, opportunities, and solutions for the project or activity.
Impact is the effect or outcome of a project or an activity on something or someone else. Impact defines how the project or activity affects or influences other factors, such as performance, quality, satisfaction, or value. Impact helps measure the success and effectiveness of the project or activity. References: CompTIA A+ Core 2 (220-1002) Certification Exam Objectives Version 4.0, Domain 5.2
Q3:
A user\’s permissions are limited to read on a shared network folder using NTFS security settings. Which of the following describes this type of security control?
A. SMS
B. MFA
C. ACL
D. MDM
Correct Answer: C
Q4:
Which of the following can be used to help recover a lost smartphone?
A. Remote support software
B. Locator application
C. NFC-enabled device
D. GPS navigation software
Correct Answer: B
Q5:
The courts determined that a cybercrime case could no longer be prosecuted due to the agency\’s handling of evidence. Which of the following was MOST likely violated during the investigation?
A. Open-source software
B. EULA
C. Chain of custody
D. AUP
Correct Answer: C
Q6:
A technician is troubleshooting boot times for a user. The technician attempts to use MSConfig to see which programs are starting with the OS but receives a message that it can no longer be used to view startup items. Which of the following programs can the technician use to view startup items?
A. msinfo32
B. perfmon
C. regedit
D. taskmgr
Correct Answer: D
Q7:
A user\’s iPhone was permanently locked after several failed login attempts. Which of the following will restore access to the device?
A. Fingerprint and pattern
B. Facial recognition and PIN code
C. Primary account and password
D. Secondary account and recovery code
Correct Answer: C
Q8:
A technician is setting up a desktop computer in a small office. The user will need to access files on a drive shared from another desktop on the network. Which of the following configurations should the technician employ to achieve this goal?
A. Configure the network as private
B. Enable a proxy server
C. Grant the network administrator role to the user
D. Create a shortcut to public documents
Correct Answer: A
The technician should configure the network as private to allow the user to access files on a drive shared from another desktop on the network
More CompTIA exam questions. . .
Updated CompTIA A+ 220-1102 learning resources
To meet everyone’s needs, 220-1102 exam resources are divided into three types of presentations:
Book
- Complete A+ Guide to IT Hardware and Software: CompTIA A+ Exams 220-1101 & 220-1102
- CompTIA A+ Core 1 (220-1101) and Core 2 (220-1102) Cert Guide
- CompTIA A+ Core 1 (220-1101) and Core 2 (220-1102) Exam Cram
https://partners.comptia.org/docs/default-source/resources/comptia-a-220-1102-exam-objectives-(3-0)
Documentation
- A+ (Plus) Certification | CompTIA IT Certifications
- A+ Core 2 (220-1102) Certification Study Guide
- Learn online with CertMaster Learn
- Apply your knowledge with CertMaster Labs
- Practice and prepare for your exam with CertMaster Practice
Doubts about the exam 220-1102
What are the most important differences between exams 220-1101 and 220-1102?
220-1101 focuses on mobile devices, networking technologies, hardware, virtualization, and cloud computing. CompTIA A+ 220-1102 focuses on operating systems, security, software, and operating procedures.
What exactly is the CompTIA A+ (220-1101 and 220-1102) exam like?
The CompTIA A+ (220-1101 and 220-1102) exams are a comprehensive collection that covers the course content of the CompTIA A+ certification Core 1 and Core 2 exams. It is designed for CompTIA A+ certification.
Is the CompTIA A+ test more difficult compared to the CompTIA test?
No, finding the right way to take the CompTIA A+ test is not difficult. For example, using CompTIA A+ 220-1102 dumps 2024 to prepare for the exam, the exam is hassle-free. When it comes to difficulty, candidates and professionals have different opinions.
Summarize:
With the CompTIA A+ 220-1102 exam, theory is important and practice is even more important. CompTIA A+ 220-1102 Dumps and CompTIA A+ 220-1102 Practice Questions You Should Have.
Listen to the advice, go and download the 220-1102 dumps 2024 https://www.pass4itsure.com/220-1102.html (PDF+VCE) 220-1102 practice questions to practice and get certified easily.