What’s new with Cisco 210-260 dumps IINS exam? “Implementing Cisco Network Security” is the name of Cisco 210-260 exam dumps which covers all the knowledge points of the real Cisco exam. 100% pass Cisco 210-260 dumps IINS exam video question description with a high score.
Pass4itsure Cisco 210-260 dumps exam questions answers are updated (280 Q&As) are verified by experts. The associated certifications of 210-260 dumps is CCNA Security. Pass4itsure offer the latest Cisco https://www.pass4itsure.com/210-260.html dumps exam material and high-quality Cisco 210-260 dumps questions & answers.
Exam Code: 210-260
Exam Name: Implementing Cisco Network Security
Q&As: 280
[New Cisco 210-260 Dumps PDF From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWU0xad3NvRWR4Qzg
[New Cisco 300-075 Dumps PDF From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWTk00ekx3V0xfX3c

Pass4itsure Latest and Most Accurate Cisco 210-260 Dumps Exam Q&As:
QUESTION 11
What are purposes of the Internet Key Exchange in an IPsec VPN? (Choose two.)
A. The Internet Key Exchange protocol establishes security associations
B. The Internet Key Exchange protocol provides data confidentiality
C. The Internet Key Exchange protocol provides replay detection
D. The Internet Key Exchange protocol is responsible for mutual authentication
210-260 exam Correct Answer: AD
QUESTION 12
A data breach has occurred and your company database has been copied. Which security principle has
been violated?
A. confidentiality
B. availability
C. access
D. control
Correct Answer: A
QUESTION 13
A proxy firewall protects against which type of attack?
A. cross-site scripting attack
B. worm traffic
C. port scanning
D. DDoS attacks
210-260 dumps Correct Answer: A
QUESTION 14
What hash type does Cisco use to validate the integrity of downloaded images?
A. Sha1
B. Sha2
C. Md5
D. Md1
Correct Answer: C
QUESTION 15
What VPN feature allows traffic to exit the security appliance through the same interface it entered?
A. hairpinning
B. NAT
C. NAT traversal
D. split tunneling
210-260 pdf Correct Answer: A
QUESTION 16
Refer to the exhibit
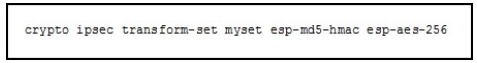
What is the effect of the given command?
A. It merges authentication and encryption methods to protect traffic that matches an ACL.
B. It configures the network to use a different transform set between peers.
C. It configures encryption for MD5 HMAC.
D. It configures authentication as AES 256.
Correct Answer: A
QUESTION 17
Which options are filtering options used to display SDEE message types? (Choose two.)
A. stop
B. none
C. error
D. all
210-260 vce Correct Answer: CD
QUESTION 18
Which accounting notices are used to send a failed authentication attempt record to a AAA server?
(Choose two.)
A. start-stop
B. stop-record
C. stop-only
D. stop
Correct Answer: AC
QUESTION 19
What security feature allows a private IP address to access the Internet by translating it to a public
address?
A. NAT
B. hairpinning
C. Trusted Network Detection
D. Certification Authority
210-260 exam Correct Answer: A
QUESTION 20
Refer to the exhibit.
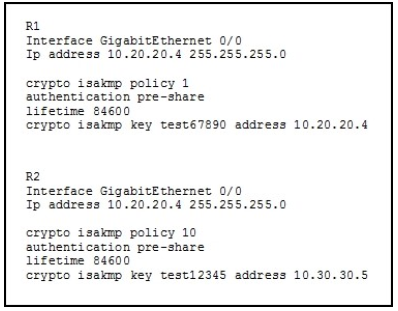
You have configured R1 and R2 as shown, but the routers are unable to establish a site-to- site VPN
tunnel. What action can you take to correct the problem?
A. Edit the crypto keys on R1 and R2 to match.
B. Edit the ISAKMP policy sequence numbers on R1 and R2 to match.
C. Set a valid value for the crypto key lifetime on each router.
D. Edit the crypto isakmp key command on each router with the address value of its own interface.
Correct Answer: A
QUESTION 21
What is an advantage of implementing a Trusted Platform Module for disk encryption?
A. It provides hardware authentication.
B. It allows the hard disk to be transferred to another device without requiring re- encryption.dis
C. It supports a more complex encryption algorithm than other disk-encryption technologies.
D. It can protect against single points of failure.
210-260 dumps Correct Answer: A
QUESTION 22
Refer to the exhibit.
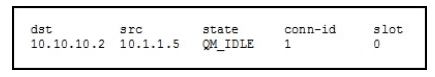
While troubleshooting site-to-site VPN, you issued the show crypto isakmp sa command.
What does the given output show?
A. IPSec Phase 1 is established between 10.10.10.2 and 10.1.1.5.
B. IPSec Phase 2 is established between 10.10.10.2 and 10.1.1.5.
C. IPSec Phase 1 is down due to a QM_IDLE state.
D. IPSec Phase 2 is down due to a QM_IDLE state.
Correct Answer: A
QUESTION 23
What is the purpose of the Integrity component of the CIA triad?
A. to ensure that only authorized parties can modify data
B. to determine whether data is relevant
C. to create a process for accessing data
D. to ensure that only authorized parties can view data
210-260 pdf Correct Answer: A
QUESTION 24
Which statements about smart tunnels on a Cisco firewall are true? (Choose two.)
A. Smart tunnels can be used by clients that do not have administrator privileges
B. Smart tunnels support all operating systems
C. Smart tunnels offer better performance than port forwarding
D. Smart tunnels require the client to have the application installed locally
Correct Answer: AC
QUESTION 25
What is the FirePOWER impact flag used for?
A. A value that indicates the potential severity of an attack.
B. A value that the administrator assigns to each signature.
C. A value that sets the priority of a signature.
D. A value that measures the application awareness.
210-260 vce Correct Answer: A
QUESTION 26
What are the three layers of a hierarchical network design? (Choose three.)
A. access
B. core
C. distribution
D. user
E. server
F. Internet
Correct Answer: ABC
Our Cisco 210-260 dumps study guide can help you pass the real exam. High-quality Cisco 210-260 dumps training materials can 100% guarantee you pass the exam faster and easier. Pass the Cisco https://www.pass4itsure.com/210-260.html dumps to obtain certification is so simple.
